In today’s digital landscape, the importance of cybersecurity cannot be overstated. As threats become more sophisticated, the demand for skilled professionals in this field is skyrocketing. This comprehensive guide aims to equip developers, IT professionals, and tech learners with the knowledge and resources needed to thrive in cybersecurity. From foundational concepts to advanced strategies, you’ll find practical applications, learning paths, and insights to help you navigate this dynamic industry.
Key Takeaways
- Understand core cybersecurity concepts and strategies.
- Explore educational pathways and certification opportunities.
- Stay updated with industry trends and emerging technologies.
- Develop practical skills through hands-on experience.
Technical Background and Context
The cybersecurity landscape is complex and requires a solid understanding of various technical concepts and methods. Here are some key areas to explore:
- Security Planning and Strategy: Develop a robust security framework that addresses potential vulnerabilities and prepares for incidents.
- Threat Detection and Incident Response: Implement systems to monitor, detect, and respond to security threats effectively.
- Access Control and Identity Management: Ensure that only authorized individuals have access to sensitive data and systems through proper identity management techniques.
- Security Compliance and Risk Management: Stay compliant with industry regulations and manage risks associated with cybersecurity threats.
- Security Testing and Vulnerability Assessment: Regularly test systems for vulnerabilities and ensure that security measures are effective.
- Incident Documentation and Reporting: Maintain accurate records of security incidents to aid in future prevention and responses.
- Collaboration and Communication: Work effectively within teams and communicate security policies and strategies across the organization.
Practical Applications and Use Cases
Understanding cybersecurity concepts is one thing; applying them in real-world scenarios is another. Here are practical applications that demonstrate how these concepts can be utilized:
📚 Recommended Digital Learning Resources
Take your skills to the next level with these curated digital products:
AI Enhanced Resume Builder
AI Resume Builder Flask App – Complete Source Code + PDF Tutorial + HTML | Digital Download for Designers
Learn AWS: Your First Cloud Application
Learn AWS: Your First Cloud Application
📊 Key Learning Points Infographic
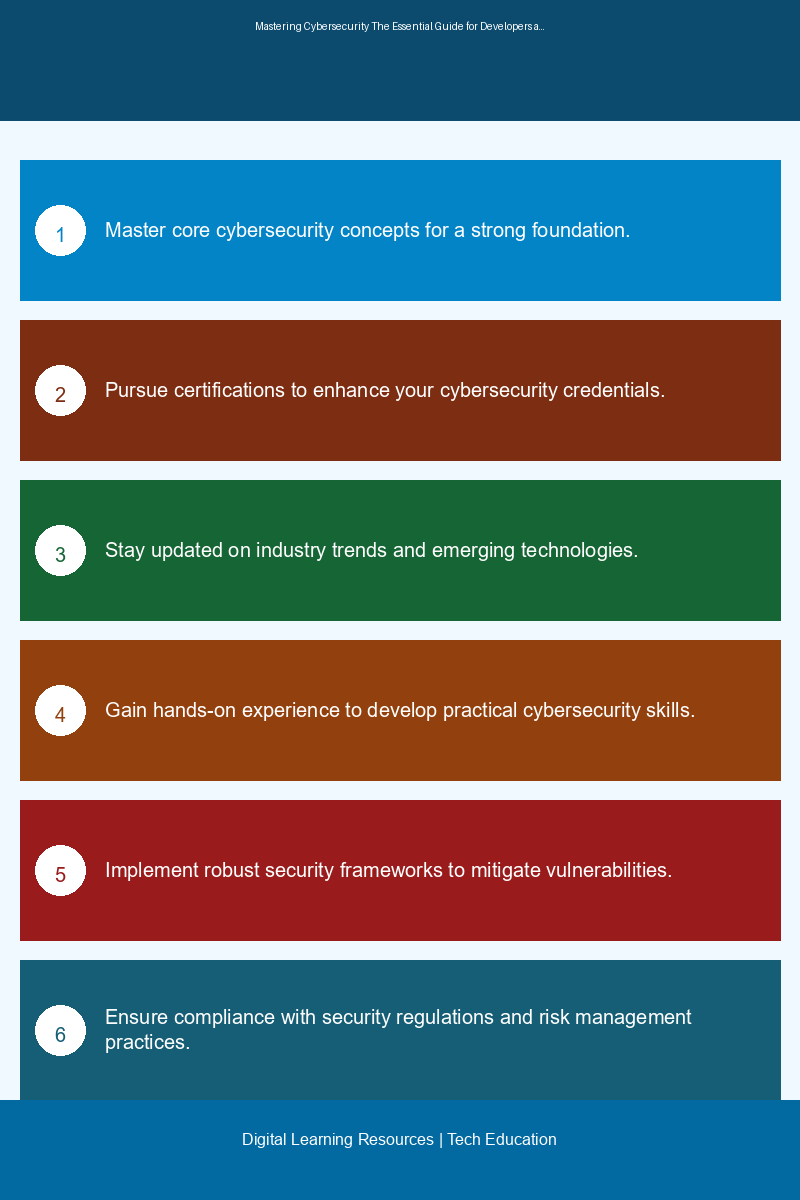
Visual summary of key concepts and actionable insights
Comprehensive SAT Prep: 470+ Vocabulary Words
Comprehensive SAT Prep: 470+ Vocabulary Words
Master DevOps in Practice – 50 Essential Topics for Engineers (PDF eBook)
Master DevOps in Practice – 50 Essential Topics for Engineers (PDF eBook)
The Ultimate Keyboard Shortcut Guide 49 Software Cheat Sheets in One PDF Bundle
The Ultimate Keyboard Shortcut Guide 49 Software Cheat Sheets in One PDF Bundle
- Security Planning: Develop a security plan for a new web application, incorporating threat modeling to anticipate potential vulnerabilities.
- Incident Response: Create an incident response plan that outlines steps for detecting and addressing breaches, including communication protocols.
- Vulnerability Assessment: Use tools like Nessus or OWASP ZAP to perform regular scans of your applications and networks to identify weaknesses.
- Access Control Implementation: Implement role-based access control (RBAC) in an organization’s system to restrict access based on user roles.
Learning Path Recommendations
To excel in cybersecurity, a structured learning path is essential. Here’s a recommended progression:
- Bachelor’s Degree: Start with a degree in Computer Science or a related field to build a solid foundation.
- Continuous Learning: Enroll in online courses, webinars, or workshops to stay updated on the latest cybersecurity trends and technologies.
- Hands-On Experience: Participate in internships, capture-the-flag (CTF) challenges, or ethical hacking exercises to gain practical experience.
- Certifications: Pursue widely recognized certifications such as CompTIA Security+, CISSP, or Certified Ethical Hacker (CEH) to validate your skills.
Industry Impact and Career Implications
The cybersecurity field is evolving rapidly, leading to a growing demand for specialized roles. Here are some industry trends and their implications for career development:
- Dynamic Nature of Cybersecurity: The ever-changing landscape requires professionals to be adaptable and quick to learn.
- Specialization: Consider focusing on specific areas such as network security, cloud security, application security, or ethical hacking to differentiate yourself in the job market.
- Career Advancement: As your skills grow, consider roles such as Security Analyst, Incident Responder, or Chief Information Security Officer (CISO).
Implementation Tips and Best Practices
To effectively implement cybersecurity strategies in your organization, follow these best practices:
- Regular Training: Conduct security awareness training for all employees to foster a culture of security.
- Incident Response Drills: Regularly practice incident response scenarios to prepare your team for real attacks.
- Use of Security Tools: Leverage cybersecurity tools such as firewalls, intrusion detection systems (IDS), and encryption to enhance security.
- Documentation: Maintain clear and concise documentation of security policies, incident responses, and compliance efforts.
Future Trends and Skill Requirements
As technology advances, so do the skills required in cybersecurity. Here are some emerging trends to keep an eye on:
- Artificial Intelligence and Machine Learning: Familiarize yourself with AI/ML applications in threat detection and response.
- Cloud Security: As organizations shift to cloud-based solutions, expertise in cloud security protocols will be essential.
- Zero Trust Architecture: Understand the principles of Zero Trust and how to implement it within your organization.
- Soft Skills: Improve collaboration, communication, and problem-solving skills, which are increasingly important in cybersecurity roles.
Conclusion with Actionable Next Steps
The journey to mastering cybersecurity is both challenging and rewarding. Here are actionable steps you can take to advance your career:
- Enroll in a cybersecurity certification course to enhance your credentials.
- Join online forums and communities to network with other professionals and stay informed about industry trends.
- Find a mentor in the cybersecurity field to guide you through your career development.
- Start applying your skills through practical exercises, such as participating in ethical hacking competitions or contributing to open-source security projects.
By following this guide, you will not only enhance your technical knowledge but also position yourself as a valuable asset in the ever-evolving field of cybersecurity. Start your journey today and take the next step toward becoming a cybersecurity expert.
Disclaimer: The information in this article has been gathered from various reputed sources in the public domain. While we strive for accuracy, readers are advised to verify information independently and consult with professionals for specific technical implementations.
Ready to advance your tech career? Explore our digital learning resources including programming guides, certification prep materials, and productivity tools designed by industry experts.